Safeguard Your Sensitive Data with GCP Secret Manager
In the realm of modern software development, safeguarding sensitive information such as database connection strings and API keys is paramount. The emergence of cloud computing has revolutionized how applications are built, but it has also underscored the importance of secure storage and usage of confidential data.
In the nascent stages of a project, it’s common to embed these critical credentials directly into the codebase or configuration files for expedience. However, this practice poses significant security risks and should be swiftly replaced with more robust solutions. Storing sensitive data within version-controlled repositories, such as GitHub, introduces vulnerabilities and compromises the integrity of the entire system.
In this article, we delve into the sophisticated capabilities of Google Cloud Platform’s (GCP) Secret Manager, offering insights into how developers can seamlessly manage and utilize confidential information within their applications. Whether deploying applications to Cloud Functions or necessitating the secure provisioning of environment variables, GCP Secret Manager emerges as a stalwart solution for safeguarding digital assets in a cloud-native ecosystem.
GCP Secret Manager
To harness the formidable capabilities of Google Cloud Platform’s Secret Manager in safeguarding your sensitive data, your initial step is to enable the Secret Manager API if you haven’t already done so.
Navigate to the Google Cloud Console and utilize the search functionality by entering “Secret Manager.” Upon locating the Secret Manager service, if it’s yet to be enabled, you’ll encounter the following interface:
Click on the “Enable” button, and within moments, the Secret Manager API will be activated. Subsequently, you’ll be redirected to the main screen of Secret Manager:

To commence, click on the “+ CREATE SECRET” button, initiating the process of adding your first confidential information into Secret Manager. This could include pivotal data like an API key essential for external service integration.
During the creation phase, you’ll be prompted to furnish basic information such as the secret’s name and its corresponding value. While Secret Manager offers various customization options like secret expiration dates and encryption settings, you can opt to retain the default configurations for simplicity.
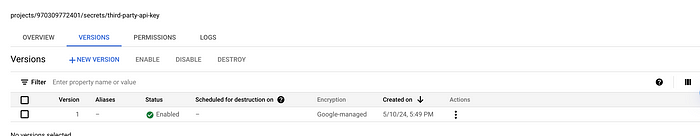
Upon successful creation, Secret Manager will display a comprehensive list showcasing different versions of the secret. Any subsequent modifications to the stored value will be systematically tracked, each iteration generating a new version labeled with an incremented numerical identifier.
Use the secret in Python Cloud Functions
To securely integrate the secret into your Python function code, you’ll first need to install the `google-cloud-secret-manager` library. This library is a prerequisite for utilizing Secret Manager across various programming languages.
For those employing Poetry as their virtual environment framework, execute the following command:
poetry add google-cloud-secret-managerFollowing the installation, proceed by creating a function designed to retrieve the most recent version of the secret for integration into your code. When invoking this function, specify “third-party-api-key” as the designated name for retrieval.
from google.cloud import secretmanager
import os
project_id = os.getenv("PROJECT_ID", None)
def get_secret(self, name: str) -> Secret:
client = secretmanager.SecretManagerServiceClient()
name = f"projects/{self.project_id}/secrets/{name}/versions/latest"
response = client.access_secret_version(request={"name": name})
return response.payload.data.decode("UTF-8")Leveraging Secrets as Environment Variables
Secrets stored within Secret Manager can be seamlessly configured as environment variables during deployment. For instance, if you intend to utilize the “third-party-api-key” within a Cloud Run application, the deployment process can be executed using the following command:
export PROJECT_ID="my-project"
export APP="myapp"
export PORT=8000
export REGION="europe-west3"
export TAG="my-app-tag"
gcloud builds submit --tag $TAG
gcloud run deploy $APP --image $TAG --platform managed --region $REGION --allow-unauthenticated --set-secrets="THIRD_PARTY_API_KEY=third-party-api-key:latest"and in the application code we can retrieve the value as a normal environment variable.
